Chapter 5
Requirement Analysis
The chapter describe security model demand and which is categorised on the footing of user interaction and specification of package and hardware demand. Besides its overview regulations assign to the assorted user.
5.1 Software Requirement
Name | Detailss |
Operating System | Windows XP and Upper |
Database Server | MySql, XML |
Front End | Netbeans 7.2, JSP, Java SDK 6.0 |
Application Server | Tomcat 6.0 |
Browser | IE 5.0 and Upper or Mozilla, Google Chrome |
Table No 4.1 Software Requirement
5.2Hardware Requirement
Name | Detailss |
Processor | Pentium IV and supra. |
Random-access memory | 256MB and above |
Hard Drive | 40 GB |
Network | Local area network |
Table No 4.2 Software Requirement
5.3High Level Process Diagrams
A high degree description of the demands of the undertaking is to manage specific defined maps utilizing a common platform, whilst other maps for content, enrollment, individuality direction, and increasing security to single applications will be outside the range of the undertaking and this range is detailed in the diagram below:
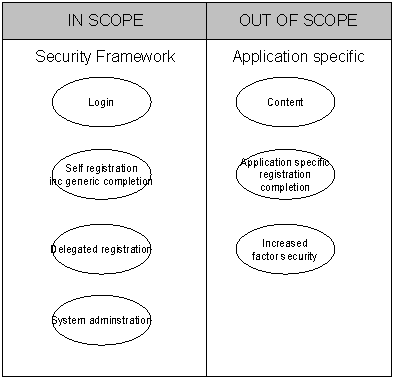
Figure 5.1: Scope of the Undertaking
This stage of the undertaking will cover individual factor hallmark and will merely capture username and watchword to authenticate a website user.
The demands are split into four subdivisions:
- Generic demands
- Self disposal functionality
- Delegated disposal functionality
- Help Desk disposal.
The generic demands will embrace certain facets that are generic across the ego disposal and delegated disposal functionality. The undertaking will present the following generic demands for self disposal and delegated disposal:
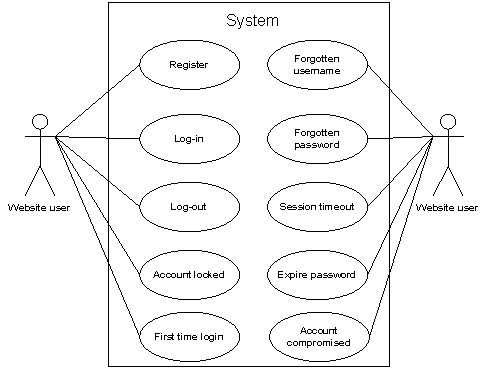
Figure 5.2: Generic demands for self disposal and delegated disposal
The undertaking will present the following self disposal functionality:
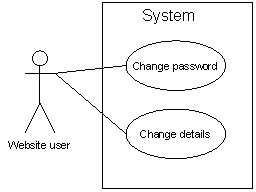
Figure 5.3: Self disposal functionality
The undertaking will besides present the followers delegated disposal functionality:
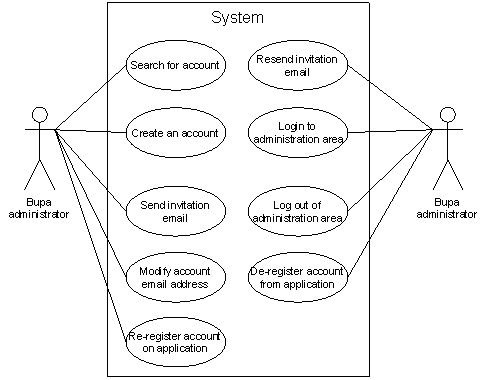
Figure 5.4: Delegated disposal functionality
There will besides be the undermentioned Help Desk disposal functionality that will be delivered by the undertaking:

Figure 5.5: Aid Desk disposal functionality
5.4 User groups
User group | Description |
External web site user | An external web site visitant to any web site or application |
Administrator | An internal decision maker who will hold the capableness to supply entree direction to application specific external web site users |
Help Desk Administrator | An internal decision maker who will hold the capableness to back up the security model and users of the model |
Table No 5.3: User Groups
5.5 Requirements
5.5.1 Generic demands
GEN-0011-Rule-2 | For Self disposal and decision maker for delegated disposal enrollment signifiers, the information Fieldss must be blank on first burden of the signifier. | ||||||||
GEN-0011-Rule-3 | The system will non auto-generate usernames for decision makers for delegated disposal. The usernames will be entered manually. | ||||||||
GEN-0011-Rule-4 | When the web site user receives the invitation electronic mail and clicks the URL to lade the enrollment signifier, the username on the signifier will be pre-populated and not-editable. | ||||||||
GEN-0011-Rule-5 | Auto-complete must be set to murder. | ||||||||
GEN-0011-Rule-6 | Password and replies to security inquiries must be obscured. | ||||||||
GEN-0011-Rule-7 | The username can non be an email reference. | ||||||||
GEN-0011-Rule-8 | The website user must put up 4 security inquiries, of which 2 will be indiscriminately shown during future hallmark procedures. | ||||||||
GEN-0011-Rule-9 | Security replies must non:
| ||||||||
GEN-0011-Rule-10 | The replies to the security inquiries will be a minimal 3 alphameric characters, with a maximal 20 alphameric characters and must non incorporate the undermentioned particular characters:
| ||||||||
GEN-0011-Rule-11 | Website users will merely be registered for applications/websites within a pre-defined group, i.e. for either BHW applications or international applications | ||||||||
GEN-0011-Rule-12 | The format of the username will be a minimal 6 alphameric characters, with a upper limit of 20 alphameric characters and must non incorporate the undermentioned particular characters:
The username will be instance sensitive. | ||||||||
GEN-0011-Rule-13 | The format of the watchword will be a minimal 8 alphameric characters, with a upper limit of 20 alphameric characters and must be instance sensitive. | ||||||||
GEN-0011-Note-1:The application specific demands for informations gaining control are non documented in this DBRS and will be documented at the application specific degree. | |||||||||
GEN-0011-Note-2:The signifier will non capture opt-in /opt-out for selling intents. This will be done at application degree and non at the security degree. | |||||||||
GEN-0011-Note-3:Website users will be able to register for specific merchandises at an application degree. | |||||||||
GEN-0011-Note-4:The website user will merely be able to take a security inquiry one time from the list, i.e. the inquiry selected in ‘Security inquiry 1’ will non look in the dropdown for ‘Security inquiry 2’ and so on. | |||||||||
GEN-0011-Note-5:Any individuality inside informations, i.e. name and reference, will be captured at an application degree. | |||||||||
GEN-0012 | Send electronic mail verification on successful enrollment to the web site user | ||||||||
GEN-0012-Note-1:A concern determination has been made to go on with the preferable option that does non necessitate email confirmation and therefore to merely hold one measure enrollment. The website users will have an electronic mail corroborating that they have registered successfully. | |||||||||
GEN-0012-Note-2: Without capturing more informations on the enrollment signifier, any electronic mails that are sent will non be customised to the website user and the salute will be ‘Dear User.’ | |||||||||
GEN-0013 | Post log-in, all designated assets ( pages ) will be protected by the Security Platform. | ||||||||
GEN-0020 | The watchword strength must be either medium or strong and must be displayed on the undermentioned signifiers:
| ||||||||
GEN-0020-Rule-1 | Mandatory ( 1 point each and a entire 2 points in the marking mechanism )
Optional ( 1 point each )
| ||||||||
GEN-0020-Rule-2 | The watchword strength saloon will expose the coloring material and besides the diction to follow with the Accessibility criterions | ||||||||
GEN-0020-Rule-3 | On page burden the watchword strength index will be clean. | ||||||||
GEN-0030 | The enrollment signifier must incorporate Captcha functionality | ||||||||
GEN-0030-Rule-1 | The Captcha functionality must follow with the Accessibility criterions | ||||||||
GEN-0030-Rule-2 | The Captcha functionality must be instance sensitive. | ||||||||
GEN-0040 | Provide registered website users with the ability to login to an application or merchandise on any web site that has migrated to the Security Framework | ||||||||
GEN-0040-Note-1:While the website user will be able to login to any web site or application, they may be required to register for each merchandise at an application degree. | |||||||||
GEN-0050 | Website users must be able to reset their watchword through disregarded watchword functionality | ||||||||
GEN-0050-Rule-1 | The website users must reply 2 security inquiry ( s ) right to reset their watchword. | ||||||||
GEN-0050-Rule-2 | The 2 inquiries will be displayed indiscriminately for the set of 4 inquiries answered on initial enrollment. | ||||||||
GEN-0060 | Website users must be able to recover their username through disregarded username functionality to reconstruct their ability to log in. | ||||||||
GEN-0060-Rule-1 | An electronic mail will be generated incorporating the website user’s username. | ||||||||
GEN-0070 | A website users account will be locked if the website user exceeds the maximal figure of login efforts or fails to reply their security inquiries right | ||||||||
GEN-0070-Rule-1 | There should be 2 error messages:
| ||||||||
GEN-0070-Note-1:The figure of login efforts and replying of security inquiries should be set to 3 efforts, so the history is locked and an enlightening mistake message is displayed. | |||||||||
GEN-0070-Note-2:For the history unlock procedure, web site users will be advised to reach the Help Desk in order to unlock their history. | |||||||||
GEN-0070-Note-2:There will be three history lock out periods. The first two lockouts will be impermanent and last for 20 proceedingss. The concluding lockout will be lasting and necessitate Helpdesk to unlock the history. | |||||||||
GEN-0080 | The system must be able to run out a web site users password at a specified interval, e.g. monthly | ||||||||
Premise:The watchword termination will be set at a generic degree and if an application requires an alternate watchword termination policy, this must be applied at the application specific degree | |||||||||
GEN-0090 | The system must be able to stop a user session after a specified period of inaction on the web site. | ||||||||
GEN-0090-Rule-1 | The in agreement length of clip for the period of inaction must be set across the platform and non at application degree. | ||||||||
GEN-0090-Rule-2 | The inaction timeout will be configured to 20 proceedingss. | ||||||||
GEN-0100 | Functionality must be provided to let the website user to log out of the Security Framework. | ||||||||
GEN-0100-Note-1:The logout user journey will be an application degree specific user journey. | |||||||||
GEN-0100-Note-2:This will be locally configurable for each concern unit. | |||||||||
GEN-0110 | Provide individual sign-on capableness such that when a website user registries for one web site or application, they are able to login to another web site or application. | ||||||||
GEN-0110-Note-1:While the website user will be able to login to any web site or application, they may be required to register for each merchandise at an application degree. | |||||||||
GEN-0120 | The system should supply scrutinizing and describing functionality of both self disposal web site users and delegated disposal web site users. | ||||||||
GEN-0120-Note-1: This functionality will be provided to the Help Desk Administrators as a portion of the Oracle Identity and Access merchandise suite. | |||||||||
GEN-0120-Note-2:Any web analytical coverage will be provided through the Omniture tool | |||||||||
GEN-0130 | The system should supply scrutinizing and describing functionality of the decision makers using the delegated disposal tools | ||||||||
GEN-0130-Note-1: This functionality will be provided to the Help Desk Administrators as a portion of the Oracle Identity and Access merchandise suite. | |||||||||
GEN-0130-Note-2:Any web analytical coverage will be provided through the Omniture tool | |||||||||
GEN-0140 | The concern units should supply an attack and procedure for managing website users concerned with possible history via media, whether this be via electronic mail or via a Call Centre | ||||||||
GEN-0150 | The system must dispute an terminal user when they:
| ||||||||
GEN-0160 | The system shall be capable of observing that a user is logging in a 2nd clip from a different topographic point, in which instance the installation should be configurable to reject the 2nd session, end the bing session, or permit coincident Sessionss. | ||||||||
Table No.5.4: Generic demands
5.5.2 Self disposal demands
Rqt No. | Description | Source/Owner | Precedence |
SA-0020 | Provide registered and logged in website users with self disposal capablenesss to alter their generic security inside informations | ||
SA-0020-Rule-1 | A website user must be able to amend the undermentioned security inside informations:
| ||
SA-0020-Rule-1 | A website user will non be able to amend the username. | ||
SA-0020-Note-1:Any application or merchandise specific informations will be amended at application or merchandise degree and as such will non be documented in this DBRS and will be documented at the application specific degree. | |||
SA-0021 | The system must direct an electronic mail to the registered web site user when an amendment has been made to their inside informations | ||
SA-0021-Rule-1 | The electronic mail must province which inside informations have been amended, butnonwhat the inside informations have been changed from or to. | ||
SA-0021-Rule-2 | If the web site user has amended their electronic mail reference, the system must direct an electronic mail to the old and new electronic mail references advising of the amendment. | ||
SA-0021-Note-1:This electronic mail will besides incorporate instructional text for the web site users in instance they are concerned that their history has been compromised. | |||
Table No. 5.5: Self disposal demands
5.5.3Delegated disposal demands
Rqt No. | Description | Source/Owner | Precedence |
DA-0010 | Provide decision makers with delegated disposal capablenesss to make an history for external web site users | ||
DA-0010-Rule-1 | decision makers will merely be able to register Website users for applications/websites within a pre-defined group, i.e. for either BHW applications or international applications. | ||
DA-0010-Rule-1 | decision makers will non be able to utilize the same username across pre-defined groups as the username must be alone. | ||
DA-0011 | Provide decision makers with the ability to advise website users of their enrollment inside informations via an invitation electronic mail | ||
DA-0011-Rule-1 | The point at which the invitation electronic mail is sent to the website user will be configurable for each application, i.e. the electronic mail may be sent when the user has been created by the decision maker or at a ulterior phase following updating of application specific history inside informations. | ||
DA-0012 | Provide decision makers with delegated disposal capablenesss to modify an bing history electronic mail reference | ||
DA-0012-Rule-1 | The system must direct an electronic mail to the registered web site user when an amendment has been made to their inside informations by the decision maker. | ||
DA-0012-Note-1:The decision maker will merely be able to modify the electronic mail reference for an history. | |||
DA-0013 | Provide decision makers with the ability to seek for an bing web site user by username and/or electronic mail. | ||
DA-0013-Rule-1 | The hunt capableness will be application degree particular and will non return users non registered for that application. | ||
DA-0014 | Provide decision makers with delegated disposal capablenesss to disenable and enable an bing history from the application | ||
DA-0014-Rule-1 | The decision maker will merely be able to disenable an bing history from the specific application the decision maker is logged into. The decision maker will merely be able to enable an history if it has antecedently been disabled from the application. | ||
DA-0014-Rule-2 | Presentment must be sent to the Help Desk decision makers when a user has been disabled for a specific application. | ||
DA-0014-Rule-3 | Presentment must be sent to the bing user when their application particular history has been enabled. | ||
DA-0015 | Provide decision makers with the ability to re-send an invitation electronic mail to a website user during the URL expiry period and post the URL expiry period. | ||
DA-0015-Rule-1 | This functionality will merely be available if the web site user has non logged in and completed their profile for the first clip. | ||
DA-0015-Rule-2 | If the invitation is re-sent during the expiry period, so the URL from the initial electronic mail will be invalid and the expiry period will be reset | ||
DA-0020 | Invitation electronic mails from the delegated decision maker must incorporate the undermentioned information for the website user:
| ||
DA-0020-Rule-1 | The URL will run out on first successful usage and the website user must alter the watchword, enter their personal inside informations, select the security inquiries and input their replies to their chosen security inquiries on login | ||
DA-0020-Rule-2 | The fresh URL should be expired after a configurable clip period and the recommendation is that this is less than 2 hebdomads. | ||
DA-0020-Rule-3 | As a lower limit the watchword must be encrypted. | ||
DA-0030 | Hard transcript invitations could be sent from the delegated decision maker and must incorporate the undermentioned information for the website user:
| ||
DA-0030-Rule-1 | The impermanent watchword will run out on first usage and the website user must alter the watchword, enter their personal inside informations, select the security inquiries and input their replies to their chosen security inquiries on login | ||
DA-0030-Note-1:The ability to capture reference inside informations for poster of the difficult transcript invitations has non been captured in this DBRS and will be documented at the application specific degree. | |||
DA-0030-Note-2:The concern procedure for the despatching of the difficult transcript invitation is out of range of the Security Platform and must be put in topographic point by the concern units | |||
DA-0040 | Provide decision makers with the screens and functionality for the delegated disposal which will be deployed at an application specific degree. | ||
DA-0060 | Provide decision makers with the ability to re-enable a user that has antecedently been disabled from the application | ||
DA-0070 | Provide decision makers with the ability to seek for handicapped users by username or electronic mail. | ||
Table No 5.6: Delegated disposal demands
5.5.4Help desk disposal demands
Rqt No. | Description | ||
SYS-0010 | Provide Help Desk decision makers with the ability to:
| ||
SYS-0010-Rule-1 | The Help Desk decision makers will be able to de-register an history at the security model degree. This will forestall the website user from logging into any application and sites. | ||
SYS-0010-Rule-2 | Presentment must be sent to each of the decision makers when a user has been de-registered at the security model degree | ||
SYS-0010-Rule-3 | Presentment must be sent to the bing user when their history has been de-registered from the Security Framework | ||
SYS-0010-Rule-4 | Presentment must be sent to the bing user when their history has been modified in any manner on the Security Framework. | ||
SYS-0010-Note-1: This functionality will be provided to the Help Desk Administrators as a portion of the Oracle Identity and Access merchandise suite. | |||
SYS-0010-Note-1:An electronic mail will be sent to the terminal user for the alteration of each property. | |||
